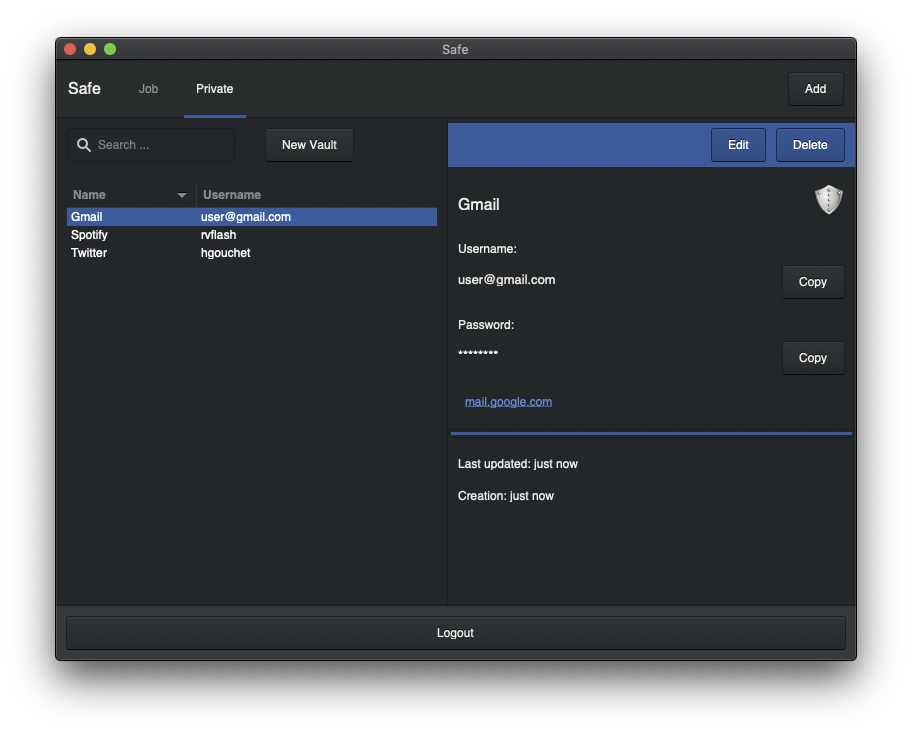
Documentation
¶
Documentation
¶
Index ¶
- Constants
- Variables
- type Data
- type Keyer
- type Login
- type OwnerService
- type Passphrase
- type Service
- type Tag
- type TagService
- type Validator
- type Vault
- func (v *Vault) AddDate() time.Time
- func (v *Vault) Key() []byte
- func (v *Vault) LastUpdate() time.Time
- func (v *Vault) Login() *Login
- func (v *Vault) MarshalJSON() ([]byte, error)
- func (v *Vault) Name() string
- func (v *Vault) SignLogin(hash crypto.Hash, l *Login) error
- func (v *Vault) Tag() *Tag
- func (v *Vault) UnmarshalJSON(b []byte) (err error)
- func (v *Vault) Valid() bool
- type VaultService
Constants ¶
const ( // MinSize is the minimum number of bytes accepted for a pass. MinSize = 16 // MaxDuration is the duration before to warn to update a data: 90 days. MaxDuration = time.Hour * 24 * 90 )
Default bounds.
Variables ¶
var ( // ErrTooShort is returned is the pass phrase is too weak. ErrTooShort = fmt.Errorf("too short, minimum required: %d characters", MinSize) // ErrMissing is returned is the mandatory data is missing. ErrMissing = errors.New("missing data") // ErrInvalid is returned if the data doesn't respect the minimum requirement. ErrInvalid = errors.New("invalid data") // ErrOutdated is returned if the data is deprecated. ErrOutdated = errors.New("outdated data") // ErrNotFound is the data doesn't exist. ErrNotFound = errors.New("not found") // ErrStrength is returned if the password is not safe. ErrStrength = errors.New("low password strength") )
List of common errors.
Functions ¶
This section is empty.
Types ¶
type Login ¶
type Login struct {
LastUpdate time.Time `json:"since"`
Name string `json:"name"`
Note string `json:"note,omitempty"`
Password string `json:"pass"`
URL *url.URL `json:"url,omitempty"`
}
Login represents the couple of username / password and any other information to sign in.
type OwnerService ¶
type OwnerService interface {
// CreateOwner creates and stores the owner of this database.
CreateOwner(p *Passphrase) error
// HasOwner returns in success if the database has a owner.
HasOwner() bool
// IsOwner returns in success if the given Passphrase matches to that of the base.
IsOwner(p *Passphrase) bool
}
OwnerService must be implemented by any service to manipulate the database owner.
type Passphrase ¶
type Passphrase struct {
// contains filtered or unexported fields
}
Passphrase is the phrase used to protect the database.
func NewPassPhrase ¶
func NewPassPhrase(s string) *Passphrase
NewPassPhrase returns a new instance of Passphrase.
func (*Passphrase) Compare ¶
func (p *Passphrase) Compare(hashed []byte) error
Compare returns in error if the given hash doesn't match with the encrypted Passphrase.
func (*Passphrase) MarshalJSON ¶
func (p *Passphrase) MarshalJSON() ([]byte, error)
MarshalJSON implements the json.Marshaler interface.
func (*Passphrase) NewCipher ¶
func (p *Passphrase) NewCipher(salt string) ([]byte, error)
NewCipher returns a hash of 32 bytes to use as AES key to encrypt data. This key is not stored.
func (*Passphrase) Valid ¶
func (p *Passphrase) Valid() bool
Valid returns in success if the key is long enough. It implements the Validator interface.
type Service ¶
type Service interface {
VaultService
OwnerService
TagService
io.Closer
}
Service must be implements by any data source.
type Tag ¶
type Tag struct {
// contains filtered or unexported fields
}
Tag is a tag.
func (*Tag) MarshalJSON ¶
MarshalJSON implements the json.Marshaler interface.
func (*Tag) UnmarshalJSON ¶
UnmarshalJSON implements the json.Unmarshaler interface.
type TagService ¶
type TagService interface {
// CreateTag creates a tag.
CreateTag(t *Tag) error
// DeleteTag deletes a tag.
DeleteTag(key string) error
// Tags lists all the tags.
Tags() ([]*Tag, error)
}
TagService must be implemented by any service to manipulate the tags.
type Validator ¶
type Validator interface {
Valid() bool
}
Validator returns in success if the data can be store.
type Vault ¶
type Vault struct {
// contains filtered or unexported fields
}
Vault stores the data (login etc.) to be protected by encryption.
func EmptyVault ¶
EmptyVault returns a empty Vault based on the given hash to sign data.
func (*Vault) LastUpdate ¶
LastUpdate returns the last update of the Vault.
func (*Vault) MarshalJSON ¶
MarshalJSON implements the json.Marshaler interface.
func (*Vault) UnmarshalJSON ¶
UnmarshalJSON implements the json.Unmarshaler interface.
type VaultService ¶
type VaultService interface {
// CreateVault stores a Vault in database.
CreateVault(v *Vault) error
// DeleteVault deletes a Vault in database.
DeleteVault(key string) error
// Vaults lists the vaults in the given tag.
Vaults(hash crypto.Hash, tag *Tag, prefix string) ([]*Vault, error)
// Vault returns the requested Vault.
Vault(hash crypto.Hash, key string) (*Vault, error)
// UpdateVault updates the given Vault.
UpdateVault(v *Vault) error
}
VaultService must be implements by any service to manipulate the Vaults.